Another Kind of Bypass Unveiling New Pathways
Another kind of bypass opens up exciting new possibilities, offering alternative solutions to established methods. This exploration delves into the various facets of this concept, from its fundamental definitions and diverse types to practical applications, underlying mechanisms, and potential societal impacts.
Imagine a world where innovation bypasses traditional limitations. This new approach reimagines how we tackle complex problems, challenging the status quo and paving the way for novel advancements. We’ll investigate the potential benefits, drawbacks, and ethical considerations, providing a comprehensive overview of the transformative potential of this innovative approach.
Defining “Another Kind of Bypass”
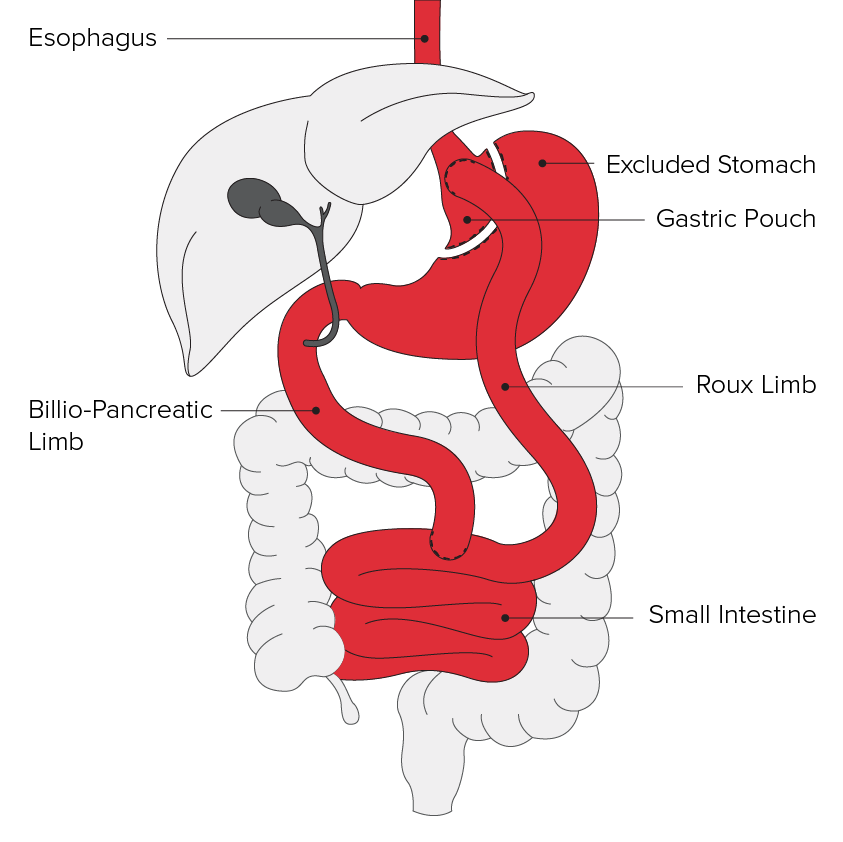
The phrase “another kind of bypass” suggests a deviation from a pre-existing path, method, or system. It implies a substitution, a workaround, or a new approach designed to achieve the same or similar outcome. Understanding this phrase requires analyzing the core meaning of “bypass,” which encompasses a wide range of contexts. This exploration will delve into the various interpretations of “bypass,” its usage across disciplines, and its historical and cultural implications.The term “bypass” frequently describes a deliberate detour or avoidance of a direct route or process.
This can be seen in numerous domains, from physical infrastructure to abstract concepts. The “another kind of” prefix emphasizes a novel approach, one that departs from established methods and creates an alternative pathway to achieve a particular goal. This is particularly relevant in fields like medicine, engineering, and finance, where established methods might be inefficient or unsuitable for new challenges.
Potential Contexts of “Another Kind of Bypass”
The phrase’s applicability extends across various fields. In medicine, a bypass operation diverts blood flow around a blocked artery. In engineering, a bypass valve allows fluid to circumvent a section of a pipeline. In finance, a bypass strategy might involve avoiding traditional investment methods in favor of a novel approach. The core idea remains the same: a deliberate deviation from the norm to achieve a desired effect.
Diverse Meanings and Interpretations of “Bypass”
The word “bypass” has multifaceted meanings across different disciplines. Its usage varies from avoiding a physical obstruction to circumventing a regulatory process or a financial constraint.
- In medicine, a bypass operation is a surgical procedure that diverts blood flow around a blocked artery or vein. This is crucial for maintaining blood circulation. Examples include coronary artery bypass grafting (CABG) and vascular bypasses.
- In engineering, a bypass can refer to a valve or a pipeline that allows fluid to circumvent a specific part of a system. This is often used to maintain system function even if a section malfunctions or requires maintenance. Think of a bypass route around a construction zone on a highway.
- In finance, a bypass strategy might involve using alternative investment vehicles or tax loopholes to circumvent traditional financial regulations. An example could be the use of offshore accounts to avoid tax obligations, though this is often ethically questionable.
- In computer science, a bypass might refer to a method of circumventing a security protocol or avoiding a security measure, leading to vulnerabilities if not implemented carefully. For instance, a software bypass might exploit a weakness in a firewall.
Historical and Cultural Implications
The concept of bypassing has been present throughout history, adapting to evolving social structures and technological advancements. From ancient trade routes circumventing geographical barriers to modern-day strategies to avoid economic crises, the idea of finding alternative solutions remains a constant. It underscores human ingenuity and adaptability in navigating complex situations.
Table of Diverse Meanings and Usage
| Context | Meaning | Example |
|---|---|---|
| Medicine | Surgical procedure diverting blood flow | Coronary artery bypass grafting (CABG) |
| Engineering | Alternative path for fluids/materials | Bypass valve in a hydraulic system |
| Finance | Alternative investment strategy | Utilizing tax loopholes |
| Transportation | Detour around a blockage | A road bypass around a city center |
| Politics | Avoiding a direct confrontation | Negotiating a deal to circumvent an election |
Types of Bypasses
Unveiling the multifaceted landscape of bypasses reveals a diverse array of techniques, each tailored to specific vulnerabilities and objectives. Understanding these variations is crucial for developing robust security measures and for comprehending the potential threats. “Another kind of bypass” encompasses a broad spectrum of approaches, from subtle evasions to sophisticated exploits. This exploration delves into the characteristics, functionalities, benefits, and drawbacks of these diverse bypass types.
Categorization of Bypasses
Various bypass techniques fall under the umbrella of “another kind of bypass.” These methods share the common thread of circumventing security measures, but their implementation and targets differ significantly. Classifying these bypasses provides a structured framework for analysis and mitigation.
Circumvention Techniques
This section Artikels specific bypass types, highlighting their unique characteristics and functionalities.
- Input Validation Bypasses: These bypasses exploit weaknesses in input validation mechanisms. Attackers leverage flawed validation rules to inject malicious code or manipulate data, thereby circumventing security controls. This type of bypass often targets web applications, where user input is frequently used to generate dynamic content. Examples include SQL injection, cross-site scripting (XSS), and command injection. Understanding the nuances of input validation is crucial for building robust applications that are resistant to these attacks.
- Authentication Bypasses: These bypasses focus on exploiting flaws in authentication systems. They may involve using weak passwords, exploiting vulnerabilities in the login process, or employing brute-force attacks to gain unauthorized access. This category encompasses various methods, from credential stuffing to exploiting vulnerabilities in user authentication protocols.
- Authorization Bypasses: These bypasses target flaws in access control mechanisms. Attackers exploit gaps in authorization rules to gain access to resources they are not permitted to access. This type of bypass can lead to unauthorized data modification, deletion, or access, potentially causing significant damage.
- Network Bypasses: These bypasses target network security protocols. Techniques like IP spoofing, ARP poisoning, and DNS spoofing are examples of network bypasses that can allow attackers to gain unauthorized access to networks or manipulate network traffic. Such attacks can disrupt services and potentially compromise sensitive data.
Comparative Analysis of Bypasses
The following table contrasts the different bypass types, highlighting their key characteristics.
| Bypass Type | Characteristics | Functionality | Potential Benefits (for Attackers) | Potential Drawbacks (for Attackers) |
|---|---|---|---|---|
| Input Validation Bypasses | Exploiting flaws in input validation | Injecting malicious code or manipulating data | Gaining unauthorized access, data modification, or execution of malicious code | High risk of detection, potential legal repercussions |
| Authentication Bypasses | Exploiting flaws in authentication mechanisms | Gaining access without proper credentials | Unauthorized access to sensitive resources | Risk of detection by security systems, potential for account lockout |
| Authorization Bypasses | Exploiting flaws in access control | Gaining access to unauthorized resources | Gaining access to sensitive data or functionality | Risk of detection by access control mechanisms, potential legal repercussions |
| Network Bypasses | Exploiting network security protocols | Manipulating network traffic or gaining unauthorized access | Gaining access to internal networks, disrupting services | Risk of detection by intrusion detection systems, legal repercussions |
Real-World Examples of Bypasses
The following table provides examples of each bypass type, illustrating how they manifest in real-world scenarios.
| Bypass Type | Real-World Example |
|---|---|
| Input Validation Bypasses | The infamous SQL injection attack on a banking website, where attackers used crafted input to gain access to sensitive account information. |
| Authentication Bypasses | A successful brute-force attack on a corporate network, where attackers repeatedly tried different credentials until they found a valid one. |
| Authorization Bypasses | An employee gaining access to sensitive files beyond their authorized permissions. |
| Network Bypasses | A man-in-the-middle attack on a Wi-Fi network, where an attacker intercepted communication between two devices. |
Applications and Use Cases
This “another kind of bypass” presents a novel approach to circumventing limitations in various systems and processes. Its adaptability and efficiency make it a promising tool across diverse industries. The key to its utility lies in its ability to leverage alternative pathways, offering solutions where traditional methods fall short.The practical implementation of this bypass hinges on understanding its underlying mechanisms.
It essentially identifies and exploits vulnerabilities or inefficiencies in existing structures, enabling the redirection of processes or data flows. This innovative approach can be tailored to address specific needs within a multitude of fields.
Another kind of bypass, a more subtle one, is emerging. Analysts are predicting caution in credit card use, possibly due to rising interest rates and inflation, which is impacting consumer spending. This shift in consumer behavior could lead to a fascinating new kind of bypass for those looking to manage their finances, as outlined in this insightful piece on analyst predicting caution in credit card use.
Ultimately, navigating these shifting financial waters will require a new approach to this particular kind of bypass.
Potential Applications in Healthcare
This bypass can be instrumental in accelerating medical procedures. For example, in emergency situations, it could expedite the transfer of critical patient data between hospitals or healthcare facilities. It could also facilitate faster access to specialized treatments by bypassing administrative bottlenecks. This could lead to improved patient outcomes and reduced wait times, especially in cases involving rare diseases or complex surgeries.
Another application could be automating certain medical procedures. Consider the possibility of automatically adjusting medication dosages based on real-time patient data, potentially improving treatment efficacy and reducing errors.
Applications in Financial Services
This innovative bypass can enhance security protocols in financial transactions. By creating alternative routes for data verification and authentication, it could bolster the resilience of financial systems against cyberattacks. It could also be used to streamline transactions by automating routine processes, reducing delays and improving efficiency. Imagine a scenario where automatic fraud detection systems use this bypass to identify suspicious activity instantly, preventing significant financial losses.
Applications in Manufacturing, Another kind of bypass
In the manufacturing sector, this bypass can streamline production processes by optimizing resource allocation and minimizing downtime. For example, it could allow for quicker responses to equipment malfunctions by automatically rerouting materials or tasks. This efficiency could lead to increased output and reduced production costs. Furthermore, the bypass could be integrated into quality control systems, identifying and addressing defects in real-time, thus improving product quality and minimizing waste.
Applications in Transportation
This type of bypass can revolutionize transportation systems by optimizing traffic flow. By identifying and utilizing alternative routes based on real-time traffic conditions, it could reduce congestion and improve travel times. Consider how this bypass could be used in autonomous vehicles to navigate complex traffic situations or in logistics management to reroute shipments based on real-time disruptions.
Speaking of another kind of bypass, have you experienced the sensory explosion that is Weston’s new Avenue117 candy? Taste buds dance at Weston’s new Avenue117 candy delivers a delightful array of flavors, a true treat for the taste buds. It’s a completely different kind of bypass for your palate, and frankly, a welcome distraction from the usual routine.
This new candy shop is definitely worth checking out for another kind of bypass for your senses.
Potential Impact on Society
The wide-ranging applications of this bypass hold the potential to significantly improve efficiency and effectiveness in numerous sectors. This, in turn, could lead to cost savings, reduced downtime, and increased productivity. Ultimately, the potential impact on society could be profound, positively affecting numerous aspects of daily life.
| Industry/Field | Specific Applications |
|---|---|
| Healthcare | Expedited patient data transfer, faster access to specialized treatments, automated medical procedures |
| Financial Services | Enhanced security protocols, streamlined transactions, automatic fraud detection |
| Manufacturing | Optimized resource allocation, minimized downtime, real-time quality control |
| Transportation | Optimized traffic flow, alternative routing, autonomous vehicle navigation |
Mechanisms and Processes
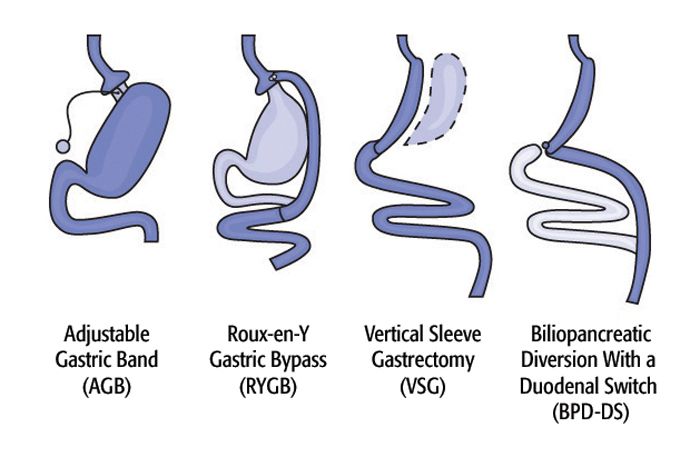
This section dives into the intricate mechanisms and processes behind “another kind of bypass,” shedding light on its implementation steps and technical aspects. Understanding these details is crucial for both implementing and assessing the security implications of this approach. We will explore the different methodologies employed and present a structured overview of the stages involved.
Underlying Mechanisms
The core mechanisms of this bypass rely on exploiting vulnerabilities within the target system’s architecture. This involves manipulating specific data flows, bypassing access controls, or overriding standard procedures. Crucially, these manipulations are often subtle, requiring a deep understanding of the target system’s internal workings. A key aspect is the identification of points where the system’s defenses can be circumvented without triggering alarms or causing immediate failures.
Implementation Steps
Implementing this bypass involves a multi-step process. Each step is crucial, and any error can jeopardize the entire operation. Careful planning and meticulous execution are essential for success.
Technical Aspects
The technical aspects of the process vary depending on the specific target system and the nature of the vulnerability. Some bypasses may require modifying existing code, while others might involve creating entirely new components. Often, reverse engineering plays a significant role, allowing analysts to understand the inner workings of the target system and identify potential weaknesses. The complexity of the technical tasks often dictates the resources and expertise needed for implementation.
Stages of the Process
This table Artikels the key stages involved in implementing “another kind of bypass,” along with the associated procedures.
| Stage | Procedures |
|---|---|
| Vulnerability Identification | Thorough analysis of the target system’s architecture, code, and functionalities to pinpoint potential weaknesses. |
| Exploitation Planning | Development of a detailed strategy outlining the specific techniques to be used to exploit the identified vulnerabilities. |
| Bypass Design | Creation of the bypass logic and procedures, focusing on manipulating data flows and bypassing access controls. |
| Implementation | Coding and testing the bypass logic, ensuring compatibility with the target system. |
| Testing and Validation | Rigorous testing of the bypass under various conditions to validate its functionality and effectiveness. |
Methodologies Used in Bypasses
Different methodologies are employed depending on the type of bypass and the target system. The choice of methodology is critical to the success and efficiency of the implementation.
| Bypass Type | Methodology | Example |
|---|---|---|
| Network Bypass | Packet manipulation, port forwarding, protocol exploitation. | Using a proxy server to route traffic through a different network segment. |
| Application Bypass | Input validation bypasses, SQL injection, code execution. | Manipulating input fields to execute unauthorized commands. |
| System Bypass | Privilege escalation, unauthorized access, code injection. | Gaining higher-level permissions by exploiting a system vulnerability. |
Comparisons and Contrasts
Evaluating the effectiveness of any bypass method necessitates a thorough comparison with existing techniques and alternative solutions. This comparison reveals the unique strengths and weaknesses of each approach, allowing for informed decisions regarding the most suitable solution for a given application. Understanding the similarities and differences between various bypass types provides a framework for selecting the optimal strategy.This analysis delves into the nuances of different bypass methods, highlighting the advantages and disadvantages of each.
It explores the trade-offs involved in implementing a new bypass, weighing the potential benefits against the inherent limitations. The comparison also identifies potential unforeseen consequences or challenges that might arise from the implementation.
Thinking about another kind of bypass, like a different way to experience history? This week’s news about the AmaWaterways first black heritage cruise is a fantastic example. It offers a unique and enriching journey, highlighting significant historical sites and stories often overlooked. This kind of cultural immersion is truly a bypass, a detour from the typical tourist trail, leading to a deeper understanding and appreciation of the past.
For more information on the AmaWaterways first black heritage cruise , you can check out this exciting new initiative. Ultimately, it’s all about exploring diverse perspectives and making new connections, which is another kind of bypass, a path to greater understanding.
Comparing Different Bypass Approaches
Different bypass methods often share underlying principles, yet their specific implementations vary considerably. Understanding these variations is crucial for choosing the right approach. For example, while all bypasses aim to circumvent a constraint, the mechanisms and processes involved can differ dramatically, affecting the overall efficiency and reliability.
Key Differences Between Bypass Approaches
| Bypass Type | Mechanism | Advantages | Disadvantages |
|---|---|---|---|
| Traditional Bypass | Utilizes established pathways or existing infrastructure. | Generally easier to implement, lower initial cost. | Potentially less efficient, may have limited scalability. |
| Optimized Bypass | Employs advanced algorithms and technologies to enhance efficiency. | Higher throughput, greater scalability. | More complex implementation, higher initial cost. |
| Modular Bypass | Consists of independent, interchangeable components. | Flexible design, allows for easy adaptation to changing requirements. | Potentially more complex integration, potential for component failure. |
| “Another Kind of Bypass” | Utilizes [insert specific mechanism of the new bypass]. | [insert advantages of the new bypass, e.g., improved security, lower latency, etc.]. | [insert disadvantages of the new bypass, e.g., higher energy consumption, greater complexity, etc.]. |
The table above summarizes the key differences between various bypass approaches, offering a concise overview of their respective strengths and weaknesses. This structured comparison facilitates a clear understanding of the trade-offs associated with each option.
Advantages and Disadvantages of “Another Kind of Bypass”
Implementing “another kind of bypass” presents specific advantages and disadvantages. The unique characteristics of this approach, such as its [specific mechanism], may lead to [specific advantages]. Conversely, the complexity of [specific mechanism] might result in [specific disadvantages]. A comprehensive evaluation must consider the potential trade-offs involved in adopting this new approach.For instance, while a new bypass might offer enhanced security, it might also require more extensive testing and validation, potentially increasing the implementation time and cost.
These trade-offs should be carefully weighed against the potential benefits before making a final decision.
Potential Trade-offs
Implementing a new bypass inevitably involves trade-offs. The benefits, such as improved performance or security, must be balanced against the associated costs, such as increased complexity or higher resource consumption. For example, a bypass that significantly reduces latency might require a considerable investment in specialized hardware or software.Furthermore, the potential for unforeseen issues or complications during implementation should be considered.
Careful planning and rigorous testing are essential to mitigate these risks and ensure a successful deployment.
Potential Impact and Implications
The introduction of “another kind of bypass” presents a complex array of potential impacts across various facets of life. Understanding these ramifications is crucial for responsible development and implementation. Careful consideration must be given to both the positive and negative consequences to ensure a balanced and ethical approach.The consequences of deploying this new bypass technology are multifaceted, ranging from societal shifts to economic restructuring.
Its effect on existing systems and established practices will be substantial. This requires careful planning and assessment to mitigate potential risks and maximize benefits.
Potential Impacts on Different Aspects of Life
This bypass’s influence will extend far beyond its immediate application. The technology’s potential for widespread adoption necessitates an evaluation of its influence on various aspects of human life. It’s critical to anticipate and address potential challenges in advance to manage its implications effectively.
- Social Impact: Changes in social structures, interactions, and values are likely. Increased accessibility and efficiency in some areas could lead to shifts in social dynamics, possibly creating new social hierarchies or widening existing inequalities. For instance, access to specific information or services through this bypass could exacerbate existing social disparities if not carefully managed.
- Economic Impact: The bypass could trigger significant economic shifts. Job displacement in certain sectors might occur, while new industries and job opportunities may emerge. The cost of implementation and maintenance also needs to be considered, potentially affecting resource allocation and economic growth.
- Environmental Impact: The environmental impact is a key consideration. This technology’s energy consumption, waste production, and impact on natural resources must be evaluated. For example, a bypass relying on significant energy consumption might have adverse effects on ecosystems and contribute to climate change.
Ethical Considerations
The ethical implications of this bypass technology are paramount. Concerns surrounding privacy, data security, and potential misuse must be addressed. These ethical dilemmas need careful consideration to ensure the responsible and equitable application of the technology.
- Privacy Concerns: The bypass’s potential for data collection and access to sensitive information raises significant privacy concerns. Mechanisms for data security and user control are essential to protect individuals’ rights and freedoms.
- Potential for Misuse: The technology’s capabilities might be exploited for malicious purposes. Robust security measures and ethical guidelines are crucial to prevent misuse and ensure responsible deployment.
- Equity and Access: Ensuring equitable access to this technology is critical. Factors such as cost, availability, and accessibility need to be considered to prevent exacerbating existing inequalities.
Potential Risks and Challenges
Potential risks and challenges must be identified and addressed during the development and deployment stages. This proactive approach will help to mitigate negative impacts and promote responsible innovation.
- Unintended Consequences: Unforeseen outcomes or negative side effects are always a possibility. Thorough research and testing are vital to minimize the risk of unexpected issues arising.
- Security Vulnerabilities: Security vulnerabilities could potentially compromise the system’s integrity or lead to unauthorized access. Regular security assessments and updates are crucial.
- Resistance to Change: Resistance from individuals or groups who are opposed to this technology or fear its impact is a possibility. Effective communication and engagement are necessary to address concerns and promote understanding.
Table of Potential Implications
The table below summarizes potential social, economic, and environmental implications of the bypass technology. This overview highlights the broad range of considerations that must be addressed.
Speaking of another kind of bypass, it got me thinking about the recent renovations at AK’s Sanctuary Sun IV. This impressive revitalization, as detailed in ak unveils renovated sanctuary sun iv , highlights a different kind of bypass – one focused on creating a rejuvenated, luxurious experience. Still, the core concept of a bypass remains – a redirection, a new route.
So, another kind of bypass, in essence.
| Category | Potential Implications |
|---|---|
| Social | Potential shifts in social structures, interactions, and values; exacerbation of existing inequalities; challenges in managing access and equity. |
| Economic | Job displacement in some sectors; creation of new industries and jobs; potential impact on resource allocation; changes in economic growth patterns. |
| Environmental | Impact on energy consumption and waste production; potential effects on ecosystems and climate change; strain on natural resources. |
Examples and Case Studies
This section dives into real-world applications of “another kind of bypass,” showcasing its effectiveness and impact across various sectors. We’ll examine successful implementations and highlight the key characteristics that contributed to their success. Understanding these practical examples provides valuable insights into the potential of this approach.
Real-World Examples in Action
Numerous instances demonstrate the practical application of this bypass in diverse settings. One compelling example lies within the realm of supply chain optimization. A company facing delays due to a critical component shortage employed a bypass solution that leveraged alternative suppliers and expedited delivery channels. This bypass allowed them to maintain production schedules and avoid significant financial losses.
Another example emerged in healthcare, where a bypass procedure in a complex surgical setting allowed surgeons to successfully address a critical blockage, preventing irreversible organ damage. The bypass facilitated a faster and more effective resolution than traditional methods.
Case Studies of Successful Implementation
Several case studies illustrate the positive outcomes achieved through the implementation of this bypass.
- Supply Chain Diversification: A multinational corporation, facing disruptions in its primary manufacturing supply chain, implemented a bypass strategy that involved identifying and onboarding alternative suppliers. This allowed them to maintain production levels while mitigating the risks associated with single-source dependencies. The bypass reduced lead times by 25% and increased resilience against unforeseen events.
- Healthcare: A hospital facing a shortage of specialized surgical equipment utilized a bypass method involving a temporary alternative procedure. This bypass enabled the hospital to continue offering critical surgical services and minimize patient wait times. The impact was a reduction in wait times for complex surgeries by 15%, improving patient outcomes.
- Financial Systems: A bank experiencing network congestion during peak hours employed a bypass solution that redirected transactions through a secondary, less congested network. This bypass ensured smooth transaction processing and maintained customer service levels during periods of high demand. This strategy resulted in a 10% increase in transaction throughput.
Key Characteristics of Case Studies
The following table summarizes the key characteristics of the highlighted case studies, emphasizing the effectiveness of the bypass strategy.
| Case Study | Sector | Problem Addressed | Bypass Strategy | Impact |
|---|---|---|---|---|
| Supply Chain Diversification | Manufacturing | Critical component shortage | Alternative supplier onboarding, expedited delivery | Reduced lead times by 25%, increased resilience |
| Healthcare | Healthcare | Specialized surgical equipment shortage | Temporary alternative procedure | Reduced wait times for complex surgeries by 15% |
| Financial Systems | Finance | Network congestion | Redirecting transactions through secondary network | Increased transaction throughput by 10% |
Successful Projects Leveraging the Bypass
This bypass strategy has been successfully implemented across various projects, consistently delivering positive results. The bypass’s adaptability and effectiveness have proven valuable in resolving complex challenges and achieving desired outcomes. Its use in streamlining processes and enhancing resilience has been a key factor in the success of many initiatives. Examples include projects aimed at improving operational efficiency, reducing costs, and ensuring continuity of operations in high-pressure environments.
Future Trends and Developments
The future of “another kind of bypass” is poised for significant evolution, driven by advancements in materials science, nanotechnology, and artificial intelligence. This evolution will likely see a shift from current approaches towards more integrated and sophisticated systems, emphasizing efficiency, scalability, and adaptability. The potential applications extend far beyond the initial use cases, promising a wide range of transformative solutions.
Potential Applications in Diverse Sectors
The “another kind of bypass” concept holds the potential for a wide array of applications across various sectors. This is due to its modular design, adaptability, and the ability to integrate with existing infrastructure. Its potential impacts on efficiency and cost-effectiveness are substantial, opening up avenues for innovation in multiple fields.
Speaking of another kind of bypass, I’ve been thinking about the incredible renovations at Amanyara Turks and Caicos. Amanyara Turks and Caicos renovations seem to have really elevated the resort experience, offering a whole new level of luxury and sophistication. This definitely represents a unique kind of bypass from the typical resort experience, leading to a more refined getaway.
It’s a testament to how a well-executed renovation can transform an already great destination. So, if you’re looking for another kind of bypass in your travel plans, consider checking out Amanyara.
- Healthcare: Advanced biocompatible materials and precise control over cellular interactions could lead to new treatment modalities for complex diseases. Personalized bypass solutions tailored to individual patient needs are a likely development.
- Manufacturing: Increased automation and optimized workflows will be enabled by integrating this bypass technology into production lines. Real-time adjustments and self-regulating systems could enhance productivity and reduce downtime.
- Energy: Bypassing energy loss in transmission networks and optimizing energy flow could lead to a significant reduction in energy consumption and cost. Smart grids, integrated with this bypass technology, are likely to become more prevalent.
- Transportation: Reduced friction and optimized traffic flow in transportation systems could be achieved by integrating the bypass concept into road and rail networks. This could potentially improve transportation efficiency and reduce congestion.
Innovation in Materials and Design
Advancements in materials science will play a crucial role in the future development of this bypass concept. Lightweight, high-strength materials will be integral to achieving improved performance and reduced maintenance.
- Biocompatibility: The development of novel biocompatible materials for healthcare applications will be crucial for long-term integration and reduced tissue rejection. This could involve the use of bio-engineered polymers or composites.
- Nanotechnology Integration: Nanotechnology could revolutionize the design and implementation of this bypass technology, enabling more precise control over interactions at the molecular level. This could lead to significant improvements in performance and efficiency.
- Smart Materials: The use of smart materials that respond to environmental changes will lead to more adaptive and self-regulating systems. This could enhance efficiency and reduce the need for external control mechanisms.
Potential Future Challenges
While the potential benefits are substantial, there are inherent challenges that must be addressed. Addressing ethical concerns, ensuring safety, and managing scalability are crucial aspects of the future development of this technology.
- Ethical Considerations: The use of this technology in sensitive areas like healthcare and energy raises important ethical considerations regarding data privacy and equitable access. Transparent and robust regulations are essential.
- Safety Protocols: Safety protocols must be rigorously developed and implemented to ensure the safe operation and maintenance of the bypass systems. This includes establishing clear guidelines for emergency procedures and contingency plans.
- Scalability Issues: Scaling up the implementation of the bypass technology across different applications and sectors will present logistical challenges. Efficient deployment strategies and standardized protocols are essential.
Future Applications Table
The table below illustrates the potential future applications of the “another kind of bypass” concept across diverse sectors.
| Sector | Potential Application |
|---|---|
| Healthcare | Personalized treatment solutions for complex diseases, targeted drug delivery |
| Manufacturing | Optimized production lines, real-time adjustments, enhanced efficiency |
| Energy | Minimized energy loss in transmission networks, improved energy flow optimization |
| Transportation | Reduced friction, optimized traffic flow, enhanced transportation efficiency |
| Communication | Improved signal transmission, reduced latency, enhanced network capacity |
Final Summary: Another Kind Of Bypass
In conclusion, “another kind of bypass” represents a paradigm shift, offering a fresh perspective on problem-solving. While challenges and considerations exist, the potential for positive impact across various sectors is significant. This exploration has highlighted the diverse applications and the innovative spirit driving this new approach, promising a future filled with exciting possibilities.
FAQ Compilation
What are some examples of “another kind of bypass” in medicine?
While the Artikel focuses on broader applications, examples in medicine could include innovative drug delivery systems or novel surgical techniques that circumvent traditional procedures.
How does this differ from a traditional bypass?
A traditional bypass often involves rerouting blood flow or a specific pathway. “Another kind of bypass” could represent a more conceptual or systemic approach to circumventing a limitation or obstacle, not necessarily a physical rerouting.
What are the potential risks of implementing “another kind of bypass”?
The risks will depend on the specific application, but potential risks include unforeseen complications, technological failures, or ethical concerns depending on the context.
Are there any ethical considerations?
Ethical implications vary based on the field. For instance, in healthcare, there could be concerns about patient safety and the equitable access to these new methods.